Understanding Secure Web Gateways
As the threat landscape continues to expand, organizations are under pressure to adopt security measures that address a wide range of web-based attacks. Secure Web Gateways (SWGs) have emerged as one of the most effective safeguards, monitoring and managing all web traffic to detect and block harmful content, enforce compliance, and guard sensitive data. SWGs act as a protective barrier between users and the open internet by inspecting requests and enforcing organizational security policies.
Beyond threat blocking, SWGs are built to ensure that employees’ web activities comply with both corporate and regulatory frameworks. This capability is particularly critical as employees increasingly access cloud apps, third-party web tools, and external resources from various locations and devices.
These gateways focus on granular policy enforcement, threat scanning, and precise rule-based protection against advanced malware, phishing, and data exfiltration. For many businesses, adopting an SWG is a foundational element of a robust security program.
Traditional firewalls alone are not adequate for defending against evasive web-based threats. SWGs deliver a specialized approach geared toward the unique risks of internet communication. In addition to protecting user data, they facilitate secure access to web resources, a crucial requirement for hybrid and remote workforces.
The Role of SWGs in Cybersecurity
Secure Web Gateways strengthen modern cybersecurity in key ways:
- Blocking Malicious Content: SWGs scrutinize inbound and outbound web traffic, filtering malware, spyware, and phishing sites before they reach users.
- Enforcing Compliance: Companies rely on SWGs to enforce acceptable use policies and comply with industry regulations governing web activity and data transfers.
- Preventing Data Loss: By monitoring outbound communications and inspecting uploads, SWGs limit the chance of sensitive or proprietary data leaking to unauthorized destinations.
- Granular Policy Controls: SWGs enable IT teams to create nuanced policies that match specific department, location, user group, and risk requirements.
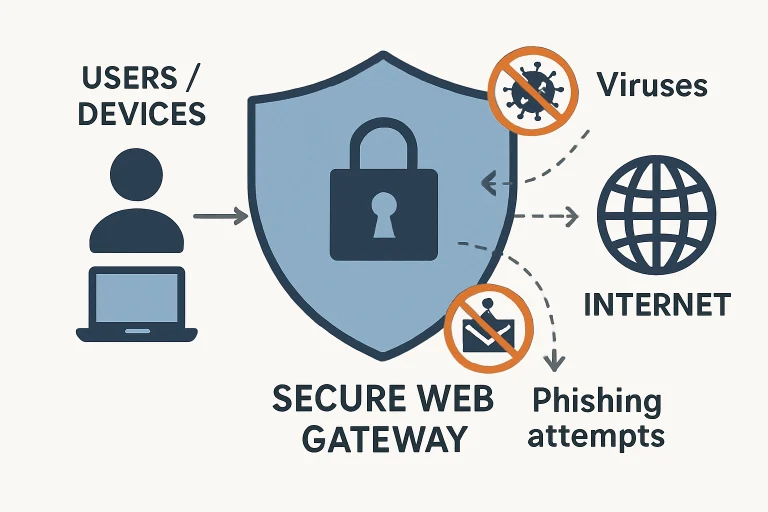
In today’s business climate, strict regulatory standards and a constant barrage of sophisticated threats make the role of SWGs more important than ever. These solutions help organizations build a security culture that not only protects information but also demonstrates due diligence for compliance audits.
Recent Developments and Challenges
Despite their wide adoption, SWGs are not without limitations or vulnerabilities. Recent demonstrations at DEF CON 32, such as SquareX revealing more than 30 methods to bypass common SWGs, highlight that even the best tools can be rendered ineffective if not updated or architected correctly. These bypasses reveal core weaknesses in underlying SWG designs, including gaps in encrypted traffic inspection and flaws in URL categorization engines. Addressing these vulnerabilities is an ongoing challenge for both solution vendors and cybersecurity professionals.
Such findings are a call to action. Organizations must demand continuous improvement from vendors and incorporate rigorous testing and validation processes into their own defense programs. The evolution of threat actor tactics means that relying on legacy approaches may create blind spots that put the organization’s environment at risk. External testing frameworks and the community-driven sharing of new threat intelligence are critical components for keeping SWGs resilient against the latest attacks.
Advancements in SWG Technologies
In response to relentless pressure from attackers, SWG vendors have been busy evolving their solutions. Innovations in recent years include advanced behavioral analytics, integration with threat intelligence platforms, and cloud-powered inspection engines. Vendors like Barracuda Networks are incorporating sandboxing features that allow suspicious web content to be opened in isolated environments, so malicious payloads can be identified and blocked before they reach users.
Another significant advancement is deep SSL/TLS traffic inspection, which allows SWGs to decrypt and analyze encrypted web sessions without significantly impacting user experience. With more than 80% of internet traffic now encrypted, this capability is essential for detecting threats that would otherwise hide from traditional filters. Cloud-based SWGs are also enabling more scalable, flexible deployments, especially important for enterprises with distributed or remote workforces.
Organizations that adopt these technologies can supplement their existing security stacks while gaining critical visibility into fast-evolving web traffic patterns. As capabilities continue to mature, SWGs are poised to become even more effective as both detection and prevention mechanisms.
Implementing SWGs in Your Organization
Assessment and Planning
Successful SWG implementation starts with a comprehensive risk and needs assessment. IT leaders should evaluate data sensitivity, regulatory requirements, user workflows, and existing infrastructure to determine the right fit for their environment.
Solution Selection
The chosen SWG must align with the organization’s scale, deployment model (on-premises, cloud, or hybrid), and integration with other security tools already in use. Flexibility to expand capabilities, such as adding advanced threat protection modules, should be considered.
Ongoing Maintenance and Education
Keeping the gateway up to date with new vulnerabilities is a non-negotiable requirement. Regular software updates, signature refreshes, and rule-set tuning help protect against emerging attacks. Equally important is providing regular staff training, ensuring they understand web security best practices alongside the technical protections in place.
The Future of SWGs
Looking ahead, SWGs are embracing artificial intelligence and machine learning to improve threat recognition and enable real-time incident response. With cloud adoption soaring and remote work now a fixture, there is a push for SWGs to expand protection beyond the traditional network perimeter, applying zero-trust principles and integrating with Secure Access Service Edge (SASE) architectures.
Enhanced threat detection, unified policy management, and protection for cloud-based apps will likely be at the heart of the next-generation SWG. These advances will help organizations stay ahead of attackers and manage the complexity arising from digital transformation initiatives.
In summary, Secure Web Gateways remain a foundational component of the modern cybersecurity arsenal. Businesses that invest in cutting-edge SWGs, commit to best practices, and prioritize ongoing adaptation will be best positioned to safeguard their operations in an increasingly risky cyber environment.

Lexy Summer is a talented writer with a deep passion for the art of language and storytelling. With a background in editing and content creation, Lexy has honed her skills in crafting clear, engaging, and grammatically flawless writing.



